Welcome to Cumulus4j!Data privacy protection: the grand challenge for cloud softwareIn this day and age, theft of highly classified data is a real threat. For example, there have been several reported cases where sensitive banking information were stolen and subsequently sold to tax authorities. Or, evidences in the media pointing to incidents where malicious hackers were able to get away with pilfered copies of huge databases from multinational companies. It is understandable that customers are worried about the security of their data and, as a result, most companies refrain from transmitting business-relevant data over the Internet to a service provider for outsourcing operational services (like invoicing or accounting). One of the most important barriers for the success of business-operational services via the Internet - software as a service - is thus the lack of data security which would guarantee that not even a system administrator can dump and sell data. Encryption for maximized data privacy protectionTo overcome this barrier, Cumulus4j aims at creating a secure architecture for trustworthy accounting software in the Internet. The demands on the trustworthy database made by an accounting software are naturally very similar to those of other enterprise applications. Therefore, Cumulus4j is an interesting solution to a multitude of applications. In order to provide a trustworthy data management, all data must be stored in an encrypted form in the cloud. Though this can already be achieved by a disk encryption software (e.g. LUKS or TrueCrypt), this solution requires the hard disk to be mounted onto the operating system before any application can operate on the data. And as soon as the disk is mounted, an internal adversary (e.g. a system administrator) can easily grab all data via the file system. 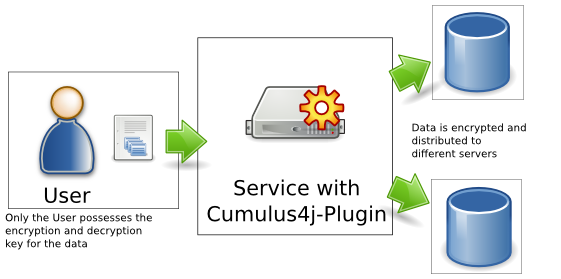 Cumulus4j solves this problem and fulfills the following requirements:
The Cumulus4j project is sponsored by the German Federal Ministry of Education and Research (BMBF) within the scope of the initiative KMU-innovativ. Cumulus4j is free software under the conditions of the AGPL. |
Documentation
AboutProject DocumentationBabelReleases |




 Deutsch
Deutsch